Radio Expert Staged the Flipper Zero Meter Attack?
Initially, I ignored the YouTube video, Flipper Zero attacking Smart Power Meters. I watched it. I thought it was “interesting.” But, I did not want to spend a lot of time on it. After all, it has been over ten years since my Black Hat / DEFCON 20 talk, Looking into the Eye of the Meter. I do not have the time, resources, or permission to do any more work on smart meters. So, I figured I would leave it to others to address the findings in this video and the person involved.
Flipper Zero Sending Commands to A1RL+ Meter
It became a little more interesting when Peter Fairlie (the apparent owner of the YouTube channel) released the next two videos titled Flipper Zero Disconnecting Smart Meter Power to House and Flipper Zero Smokes Smart Meter ! and they started getting more media attention. In these videos the Flipper Zero is used to run two commands. For the first command, the Flipper Zero is set to operate in the 902 – 928 MHz range and to send a file “D” (changes slightly in different videos) which appears to start the communications with the meter. It can be presumed that this file contains packetized commands which are modulated and transmitted to the meter. Once these bytes are received by the meter, an A1RL+ in the first and second videos and a A3TL in the third video, the meter appears to go into a test mode and cycles through multiple displays on the meter’s Liquid Crystal Display (LCD). The second script run by Peter, titled “sudo SHUTDOWN NOW”, is represented to have “disconnected” the meter resulting in a power outage for the home. This “disconnect” condition is a lie.
In truth, as explained to me by Dr. Emma Stewart, an expert in electrical and smart grid technologies, neither of these meters have a disconnect feature built into them. It is physically impossible for them to “disconnect” and permanently deenergize the home. She pointed me to the technical manuals for the ALPHA Plus Meter (A1RL+) Technical Manual and ALPHA A3 ALPHA Meter (A3TL) Technical Manual which explain the meter’s base functionality with no description of a disconnect feature.
The result of the Flipper radio transmission on the meter appears to cycle the operating mode of the meter resulting in loud physical clicking from the meter and the house deenergizing and reenergizing in a cycle until the meter stops the cycle or resets. The documentation for the A3TL and A1RL+ does not specifically explain a test mode that would cause this behavior. It is possible that there is an undocumented test. It is also possible that the data received by the meter, from the Flipper Zero, resulted in this cycle. As to why the A3TL meter started smoking during one of these operations it cannot be determined without a more detailed physical inspection of the meter.

Smoke Coming Out of Meter
To understand this situation better it is important to understand the equipment that is being “attacked” in these videos. The Elster A3TL and A1RL+ are electric meters that are a bit more advanced than the old meters with spinning dials. While more advanced than these older models, the A3TL and A1RL+ are not considered Smart Meters. Smart meters are devices that are deployed as a part of an Advanced Metering Infrastructure (AMI) project that provide significantly more capabilities and communications with the utility’s remote management infrastructure. The A3TL and A1RL+ meters were designed to operate on their own or, if configured with a communication module like the Elster ALPHA STARS Wide Area Network (WAN) option board, as a member of an Automated Meter Reading (AMR) deployment. The primary difference between the AMI and AMR technologies is that the AMI meters communicate back to the utility through radio gateways and can be programmed to respond to different conditions when these communications are not available. AMR meters, like the ones in the videos, require utility personnel to collect the information from the meter by driving a radio near the meter. The AMR meters have very limited programmed functionality primarily limited to self-tests to provide information to operators without the need to connect external analysis tools making maintenance safer and faster.
Now that we understand the meters a little bit better, the next question is why Peter is testing the meters on the side of his home (and, presumably, a neighbor’s house). The answer is he is not testing the smart meter installed on his home. He wants the viewers to think he is testing a smart meter but he is using the old ‘bait-n-switch’ trick. The meters, used in each video, can be easily purchased on eBay for $25.00 as shown in the following image. The meter in this image is a “non-AMR” meter meaning that it most likely does not come with a communications radio. It is very likely that Peter purchased one of these meters, possibly with a communication module. Then, after conducting some research, Peter replaced his home’s meter (or smart meter) with the purchased meter.
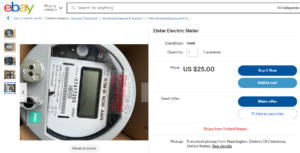
Meter for Sale on eBay
The electric meter seals on the meters in the videos make it seem like the meters have not been removed and are in the original condition as installed by the local utility. However, like the meters, these seals can be purchased online. The following image shows yellow electric meter seals, like those on the meters in the videos, can be purchased on Amazon for $25.00.
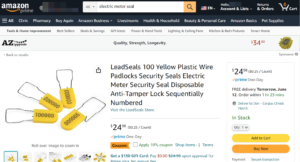
Electric Meter Seals on Amazon
Peter appears to have purchased several of these meters and is using them to test meter communications by connecting them to his home in Canada (deduced from OSINT taken from his other videos in his YouTube channel). This is not surprising as Peter appears to have a passion for hacking technologies with radios and in his job as the Chief Technology Officer (CTO) for First Mile Technologies which provides radio communication in many of their solutions.
The problem I have with the information presented in these videos is that it is purely Fear Uncertainty and Doubt (FUD). Peter obtained decommissioned and irrelevant meter technology and purposely represented his research as destructive and a threat to societies deploying smart meters. Worse, it rekindles the arguments of smart meter conspiracy theorists and politicians which forces smart meter researchers, industry professionals, and vendors to waste valuable cycles on disproving his claims. These professionals have more important tasks defending Canada’s and the United States’ critical infrastructure. They should not be wasting their time on someone grubbing for YouTube subscriptions and ‘for the LULZ.’ The testing shown in these videos can also lead other people to think that testing the meters on their homes is acceptable. The unauthorized testing of meters is illegal and people testing meters owned by a utility will most likely be subject to prosecution.
My recommendation to people conducting authorized meter and radio research is to avoid creating controversial videos and blog posts to attract attention. I encourage all of you to create technical content that explains what you are doing and how you are doing it. Open source research is extremely important for all industries but the research steps and results should stand on their own merits without sensationalistic claims. Additionally, when issues with critical infrastructure technologies are found I recommend that you follow responsible disclosure recommendations using vulnerability disclosure services provided in the Canada authorities and US CISA. These teams have the means to notify vendors in a manner that allows them to understand the situation and produce remediations that prevent and detect attacks. This is how your hard work can help protect your society and ensure you get the electricity you need to continue your research, jobs, and hobbies.
Finally, I MUST say something about the dangers of doing research on meters. Meters are very dangerous devices that can, and will, kill you. The internal components of these devices contain capacitors that store enough energy to stop your heart several minutes after they have been unplugged. Do not open these devices without the proper training on the internal electrical components. The best way to test these types of devices is to get a job with one of the many vendors that produce smart grid technologies or with a utility. These organizations are looking to hire and train people to improve the security of industrial solutions and their implementation. A quick search on Google or Linked In will provide you with a long list of opportunities for new and experienced positions.
Go forth and do good things,
Special Thanks
I would like to give a special thank you to the following people who helped review this situation and blog post with me. Their support was invaluable.
Resources
- Meter on eBay $25.00: https://www.ebay.com/itm/234964453806?hash=item36b4f909ae:g:h54AAOSwRCJkMZtl
- Electric Meter Seal on Amazon $25.00: https://www.amazon.com/LeadSeals-Padlocks-Disposable-Anti-Tamper-Sequentially/dp/B0BZ71M57J
- Elster Form 16S A3 ALPHA Meter / Collector Emissions Test Report: https://device.report/m/9acaec0d1022c1b1fe5cfcfa356ad2221c9ccf61bd3467c97982db7542fecb98.pdf
- Elster Form 4S REX Meter Emissions Test Report: https://device.report/m/58a891a0a6b0a4f310030dd2af1a53f5452ea9f8af50b9f8a6cd9034bba5751a.pdf
- Flipper Zero attacking Smart Power Meters: https://www.youtube.com/watch?v=K3_0XHlCEQg
- Flipper Zero Disconnecting Smart Meter Power to House: https://www.youtube.com/watch?v=lwR02fkLfhU&t=2s
- Flipper Zero Smokes Smart Meter!: https://www.youtube.com/watch?v=kF6o9Ec4k_o&t=210s
- ALPHA Plus Meter Technical Manual: https://www.guggenmossales.com/documents/PowerPlus-TM42-2182C.pdf
- ALPHA A3 ALPHA Meter Technical Manual: https://guggenmossales.com/documents/A3MeterTM42-2190BUSVersion.pdf


